
Created by Michelle for OLLI@WVU 1
Facebook
User Tracking .................................................... 1
Unique Identifiers ............................................. 1
Web Cookies ..................................................... 2
Privacy .............................................................. 2
Facebook Controversies ................................... 2
World-Wide Election Meddling ....................... 3
Cambridge Analytica (2014-2018) ................... 4
Anti-Trust? ....................................................... 4
Censorship ........................................................ 5
Public Discourse and Mental Health ............... 6
And Yet… .......................................................... 6
Making Your Facebook Use More Secure ........ 7
Using Facebook ................................................ 8
Posts .................................................................. 8
News Feed ......................................................... 8
Facebook Settings ............................................. 9
Notifications ................................................... 10
How to Delete Facebook .................................. 11
Facebook Website ............................................ 12
News Feed (Browser) ...................................... 12
News Feed Preferences (Browser) .................. 12
Writing Posts (Browser) ................................. 14
Editing Posts (Browser) .................................. 14
Settings (Browser) ........................................... 15
Apps within Facebook (Browser) ................... 20
Messenger (Browser) ...................................... 20
Facebook App on Android .............................. 23
News Feed (Android)...................................... 24
Posts (Android) ............................................... 26
Facebook App on iOS ..................................... 28
News Feed (iOS) ............................................. 29
Posts (iOS) ...................................................... 29
Facebook Settings (iOS) ................................. 30
Location Settings (iOS) .................................. 30
Web Browsers ................................................. 32
Web Browser Add-Ons ................................... 32
Phone Apps ..................................................... 32
Emoticons ....................................................... 33
Acronyms ........................................................ 34
Technology Glossary ....................................... 35
References ....................................................... 48
Index ................................................................ 51
Jump directly to the section on Using Facebook
User Tracking
You’ve probably noticed that when you shop for something on one website, ads in Facebook
immediately appear for whatever it is you were just looking for. This is not a coincidence but it’s not
black magic either. In short, it comes down to primarily two things (there are others, but these are the
important ones): unique identifiers and web cookies.
Unique Identifiers
If you want to understand how to make your online presence more secure and more private, you need
to understand the basics of how companies collect and collate your data in the first place.
When you log into Facebook, your login credentials require your email address. This email address is
your unique identifier.
How do companies use this to collect information? Because this email address is associated only with
you, every time this email address appears in an advertiser database, it can be directly linked to your
Facebook account. So if you use the same email address for everything, all data you have shared with
each of those companies could become aggregated into a single file.
Just how important are these unique identifiers to Facebooks business model? When Apple rolled out
its iOS with App Tracking Transparency in 2021, Facebook estimated that change would cause
Facebook to lose around $10 billion dollars.
Created by Michelle for OLLI@WVU 2
Web Cookies
In electronic terms, cookies are not a delicious baked good, but are instead bits of code that hold
information about what you are doing. Cookies are what allow you to place an item in your online
shopping cart, browse around for other items, and then purchase all those items at one time. Without
cookies, the web would not be particularly interactive, because your information could not be saved
from one page view to another.
Unfortunately, cookies can be used by “third parties” to track what you are doing, and Facebook does
a lot of this. If you see a Facebook “Like and Share” button on a web page, then Facebook is collecting
information about what you are doing on that page.
Facebook collects this information whether you have a Facebook account or not.
Facebook collates and uses this information whether you have a Facebook account or not.
Privacy
In 2022, Facebook turned over Messenger chat records to the Nebraska police after being served with
a warrant.
Apps Sharing Personal Data ( - 2019)
• Apps shared data with Facebook, including private health information like women’s periods
and pregnancy attempts.
• Apps shared this data with Facebook even if the user DID NOT have a FB account.
Facebook Controversies
Facebook requires that users be who they say they are, which theoretically allows the company to
remove suspicious users and fake accounts, however, that has not stemmed the tide of fake news,
violence, fake accounts, and hate speech that has been one of the more controversial aspects of the
site.
Many major controversies stem from privacy and issues and concerns and scandals, where Facebook
has made the supposedly private data of users available to advertisers and analysts.
Scams
• Scam ads
• Hidden statistics about people viewing your profile
• Look at this embarrassing video of you!
• Shocking news & headlines
Retaining users’ deleted videos (2018)
Even if a user deleted their video, that content still remained on Facebook’s servers.
Data-Breaches 2018-2021
A data breach is when protected information is accessed by unauthorized parties. This can come from
a bad actor breaking into a database, or from a security failure, such as a website failing to protect and
encrypt data tables.
Created by Michelle for OLLI@WVU 3
• June 2013: personal data of 6 million users (1%) exposed
• May 2018: private posts of 14 million users (1%) made public
• September 2018: attackers gained access to 50-90 million user (2-4%) accounts
• March 2019: 600 million (25%) passwords saved in plaintext
• April 2019: 540 million (22%) records found on a public server
• April 2019: Facebook harvested email contacts of 1.5 million new users
• September 2019: 419 million (17%) user ID, phone number full name, gender, location found
on an exposed server
• December 2019: 309 million (12%) phone numbers, names, user IDs found on an exposed
server
• April 2020: 267 million profiles sold on the dark web for $540 (five hundred and forty dollars).
• April 2021: 533 million profiles (19%) names, addresses, phone numbers, birthdays etc from
users in 106 countries were posted for free on a forum.
(%) the percent of all active Facebook users affected
Scraping Public Profiles
At one point this data could have included: email address, phone number, location, attended events,
liked pages, groups, photos, and all public comments and posts. This data can then be linked to all
other kinds of public records (ie voter records) as well as behavior on other websites.
Even if a person leaves social media—or never joins—the posts of their friends give “potential
predictive accuracy” of 95% of their future activity.
World-Wide Election Meddling
In 2020, low-level data scientist Sophie Zhang turned down a $64k severance package requiring an
NDA to write an 8,000-word exit memo when she left Facebook. In it she gave evidence of how
Facebook has made election interference both common and easy, and how Facebook ignored the
problem.
Rohingya (2018-2019)
Incitement of genocide against Rohingya in Myanmar (2018) resulting in the murder of over 24,000
Rohingya and the creation of over 700,000 refugees in Bangladesh.
In Myanmar, the Facebook app was so popular, people used Facebook and internet interchangeably.
India (2019-2021)
An anonymous Facebook employee created a test account to follow groups and pages in India that
were promoted by the platform (and only those groups and pages). In less than three weeks their feed
was swamped with hate speech and viral content, including violence and gore (such as a beheaded
man). Additionally, both Facebook and WhatsApp were accused of helping to spread hate speech and
fake news, including posts that led to a riot that killed 53 people.
Russian Meddling
Russians created thousands of social media accounts pretending to be Americans, paid for Facebook
ads during the 2016 campaign that reached 126 million FB users. These ads were not just pro-Trump
and anti-Clinton, but aimed at manipulating Democratic voters as well, with campaigns to skip voting
or use bogus voting methods. See also: Cambridge Analytica.

Created by Michelle for OLLI@WVU 4
Cambridge Analytica (2014-2018)
Readers took a “personality” survey through a downloaded app, which also scraped data from their
profile AND the profiles of their friends. Only 270k users took the survey and consented to data
harvesting, however Cambridge Analytica collected data on over 50 MILLION users.
• 2016 US Election (Trump, Cruz)
• Brexit Vote
• 2018 Mexican General Election (IDP)
We also got access to census data. Unlike developing nations with less stringent privacy controls, the U.S.
government won’t provide raw data on specific individuals, but you can get information, down to the county
or neighborhood level, on crime, obesity, and illnesses such as diabetes and asthma. A census block
typically contains six hundred to three thousand people, which means that by combining many sources of
data, we could build models that infer those attributes about individuals. For example, by referencing risk or
protective factors for diabetes, such as age, race, location, income, interest in health food, restaurant
preference, gym membership, and past use of weight-loss products (all of which are available in most U.S.
consumer files), we could match that data against aggregated statistics about a locality’s diabetes rates.
We could then create a score for each person in a given neighborhood measuring the likelihood that they
had a health issue like diabetes—even if the census or consumer file never directly provided that data on
its own.
-- Wylie, Christopher. Mindf*ck (2019)
Anti-Trust?
Facebook (like most other tech companies) has a record of gobbling up smaller companies. However,
it is documented that Facebook acquired many of these smaller companies because they saw them as
competition.
Meta, Facebook’s parent company, owns the following companies:
Facebook
Giphy
Instagram
Messenger
Oculus VR
Threadsy
WhatsApp
Onavo
CTRL-labs
It also owns a number of companies you have never heard of, such as those for created for marketing,
advertising, mobile, and many many more.
Theoretically, these purchases could be seen as allowing Facebook to create a better product, however,
there are two important things to note.
First, in a pending case filed in 2021, the FTC alleged:
“Facebook’s actions have suppressed innovation and product quality improvements. And they have
degraded the social network experience, subjecting users to lower levels of privacy and data
protections and more intrusive ads. The FTC’s action today seeks to put an end to this illegal activity
and restore competition for the benefit of Americans and honest businesses alike.”

Created by Michelle for OLLI@WVU 5
This case is still ongoing.
Second, some of this can be glimpsed in actions taken by Facebook after acquisition, when the
company took actions that were often in direct opposition to stated goals of the founders.
Advertising isn't just the disruption of aesthetics, the insults to your intelligence and the interruption of
your train of thought. At every company that sells ads, a significant portion of their engineering team
spends their day tuning data mining, writing better code to collect all your personal data, upgrading the
servers that hold all the data and making sure it's all being logged and collated and sliced and
packaged and shipped out... And at the end of the day the result of it all is a slightly different advertising
banner in your browser or on your mobile screen.
Remember, when advertising is involved you the user are the product.
-- WhatsApp Blog, 2012
A re-share button would give Instagram less power to demonstrate model behavior; everyone would
just be focused on going viral.
…
The founders thought it would violate the expectations you had when you followed someone. You
followed them because you wanted to see what they saw and experienced and created. Not someone
else.
-- Sarah Frier No Filter (2020)
Censorship
Censorship is defined as “a system in which an authority limits the ideas that people are allowed to
express and prevents books, movies, works of art, documents, or other kinds of communication from
being seen or made available to the public, because they include or support certain ideas”
It is important to note that censorship is illegal only when the government engages in it.
Congress shall make no law respecting an establishment of religion, or prohibiting the free exercise
thereof; or abridging the freedom of speech, or of the press; or the right of the people peaceably to
assemble, and to petition the Government for a redress of grievances.
– The First Amendment to the U.S. Constitution
Categories of speech that fall outside protection are:
• hate speech
• child pornography
• defamation / slander
• incitement to violence
• true threats of violence.
Individuals and non-governmental groups (which includes social media sites such as Facebook) are
entirely within their rights to remove any content they want.

Created by Michelle for OLLI@WVU 6
The problem with Facebook’s content moderation is that it is uneven and frequently biased. There are
a variety of reasons for this, including (but not limited to):
• Community moderators are generally outsourced to other countries
• Automatic bans certain types of pictures, such as breasts, even of those pictures are historical
artwork or medical posts
Additionally, problems are caused by Facebooks algorithm which populates news feed. This algorithm
promotes content that gains attention (likes, shares, and comments) rather than content based upon
your interests.
• Elites are regularly exempt from content moderation by the sites “cross check” or XCheck,
which at one point exempted 5.8 million users
• Activists are often suspended for pointing out hate speech and racism
Is Facebook now a quasi-public space? Chuck Johnson lost a similar case against Twitter in 2018.
Public Discourse and Mental Health
In 2021, whistleblower Frances Haugen released copies of confidential documents, showing that
Facebook hid the harms it knew the site was causing, instead focusing on growth rather than
safeguarding its users.
How does this work?
A post that receives high “engagement” (likes, shares, and comments) is promoted in user feeds, and
research found the posts that have the most engagement are negative ones—posts that are “hateful,
divisive and polarising.”
Facebook made a heralded change to its algorithm in 2018 designed to improve its platform—and
arrest signs of declining user engagement. Mr. Zuckerberg declared his aim was to strengthen bonds
between users and improve their well-being by fostering interactions between friends and family. Within
the company, the documents show, staffers warned the change was having the opposite effect. It was
making Facebook, and those who used it, angrier. Mr. Zuckerberg resisted some fixes proposed by his
team, the documents show, because he worried they would lead people to interact with Facebook less.
-- The Wall Street Journal (2021) The Facebook Files
Emotional Manipulation
A 2014 study published in the PNAS found that user responded to the tone and emotion of posts they
saw in the Facebook News Feed. When the feed was manipulated to show more positive items, users
responded with more positive posts of their own. When the feed was manipulated to display negative
items, users were more likely to post their own more negative content.
And Yet…
Despite these issues, Facebook does have the potential to be a force for good, allowing people to
remain in contact across distances in a manner that was unimaginable a half century ago. It has also
been useful in emergencies, allowing affected individuals to “check in” and let friends and family
know they are safe, which could help to reduce some of the burden on phone lines and cell towers
during such times.

Created by Michelle for OLLI@WVU 7
Making Your Facebook Use More Secure
Here are the top things you can do to make using Facebook safer:
• Do NOT use the Facebook app on your phone. Use a web browser on your phone instead.
• Do NOT use the Facebook Messenger app on your phone.
• Install a browser on your computer / device that you ONLY use for Facebook.
• Go through all your Facebook privacy settings.
• Do NOT use Facebook to log into other websites; create unique login credentials for every site.
• Regularly remove third-party apps permissions.
• Use privacy and security add-ons to restrict access to your browsing history.
• Create and use an email account that is unique for Facebook.
Created by Michelle for OLLI@WVU 8
Using Facebook
Facebook looks (and sometimes works) differently, depending upon whether you are using a
computer or a mobile device. And the Facebook app does not look the same on iOS devices as it does
on Android devices.
The rest of the document is divided into parts: Facebook on a computer, the Facebook app on an
Android device, and the Facebook app on an iOS (apple) device.
At the end of the document are and references to help you translate a little bit of what you’ll see
online.
Posts
There are typically two ways you can post to your timeline: writing a post, or sharing a post from
another person or group. When you create or share something on your timeline / wall, that post is
displayed on your wall.
Anything you post on your wall—even something you are sharing from someone else’s wall, gets its
own comment section on your wall. This means that comments you make on posts on other people’s
walls will not appear on your wall.
Public vs Friends vs Groups
Your posts can have four levels of accessibility: public, friends, specific friends, and only me.
Public
Friends
Selected Friends
Only Me
Posting something to the public means that anyone in the world who access Facebook can see what
you posted. Friends means that the post will be visible to everyone in your friends list. Selected
Friends posts are displayed to a group or a handful of friends. Only Me is precisely what it sounds like.
If you change the post visibility when you are creating the post, that setting will “stick” and be the
setting for all posts going forward. You do have the ability to change the visibility of a post after it has
been created, and in usually this is easier than trying to remember to change the visibility the next
time you post.
News Feed
Your News Feed displays posts from family and friends as well as groups and businesses you have
liked and/or followed. The News Feed is the main part of Facebook—it’s what you see when you first
log into the website.

Created by Michelle for OLLI@WVU 9
You have two options to make minor modifications to this. One is to hide posts by specific groups or
individuals, and the other is to toggle see first for specific pages or individuals.
Hiding Posts
Hide post
Hide this specific post from your wall / news feed. This is good if you want to ignore a single,
specific post.
Snooze for 30 days
Hide posts from this person for a month. This is something that is useful in the month before an
election.
Hide all from / Unfollow
This allows you to stop seeing posts from someone, but still remain friends with them; you can see
their posts by going to their wall.
Facebook Settings
Over the years, Facebook settings have gotten more and more complicated making it is sometimes
difficult to find a specific setting. Use the search function whenever possible—the location of any
setting has probably changed since they last time you checked it.
Activity Settings
Friend Requests
Setting this to Friends of friends limits the audience of people who can make friend requests,
however, it means that if you don’t have friends in common, you can’t receive a friend request from
someone.
Friends List
This sets who can see your list of friends.
Profile Visibility to Search Engines
Do you want your Facebook page to come up in a google search of your name? My answer is no. You
have to decide this for yourself.
Who Can Post on your Timeline
This allows you to restrict who want leave messages on your wall / timeline. If you have family
members who passive-aggressively share things on your timeline, restricting this might be useful.
Tagged Post Visibility
If someone tags you in a post, who do you want to see that post?
Review of Tagged Posts
If someone tags you in a post, do you want to OK it before other people can see it?
Off-Facebook Activity
Facebook has a privacy / security setting that allows you to see how you are being tracked by third
parties when you are not actively using the Facebook site. I highly recommend you peruse and clear
this list, as well as turning off future tracking (Disconnect future activity). Off-Facebook activity
Location History
Location history is for the Facebook app on your mobile device. Through the website you can toggle it
on or off.
Comments
Notifications when someone comments on one of your posts.

Created by Michelle for OLLI@WVU 10
Tags
Notifications when someone names in a comment on a post.
Logged Actions
Why does Facebook seem to know everything about you? Because it tracks and logs everything you
do. I recommend going through your logged actions and clearing all history.
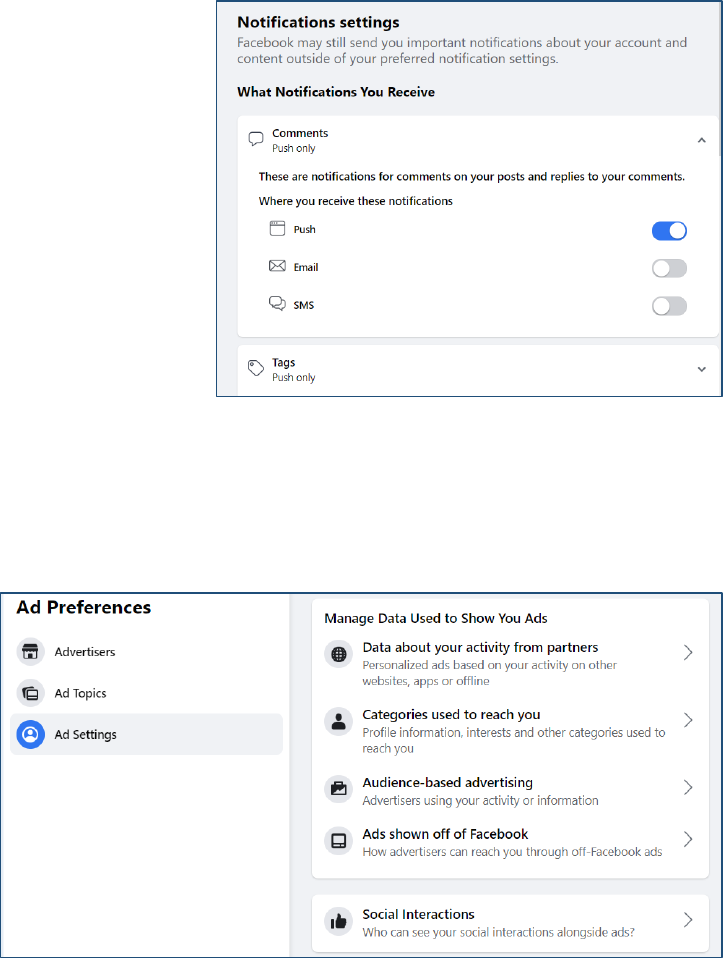
Ad Preferences
Ad Preferences are where you can set your ad preferences. Unfortunately, this does not stop Facebook
from collecting data on you from other websites, it only keeps Facebook from (theoretically) using
that data to give you tailored ads.
To reduce the amount of tracking Facebook does, you will need to delete the Facebook apps from your
smart devices, change your unique identifiers (email and phone number), and takes steps to block
Facebook cookies within your web browser(s).
Partner Data
Personalized ads based on your activity on other websites, apps or offline.
Demographic Categories
Ads shown off of Facebook
Can advertisers choose to reach you through ads off Facebook.
Social Interactions
This allows your friends to see if you have liked or interacted with a product or brand.
Video Auto-Play
Does a video automatically start playing as you scroll past?
Password
Two-Factor Authentication
Do you use two-factor authentication to access the website?
Notifications
Notifications are updates you can receive about what has happened on Facebook. By default,
Facebook wants you to know ABSOUTELY EVERYTHING ALL THE TIME. This is designed to keep
you using Facebook and can be overwhelming.
I highly recommend turning off SMS and Email notifications. This helps keep you from being
constantly pulled back into Facebook.
• Red Alert Notifications: Notifications that appear above the bell icon. When you have a new
notification, a red bubble will appear with the number of new notifications you've received.
• SMS Notifications: Notifications that are sent to your phone via text message.
• Email Notifications: Notifications you receive via email. Facebook sends a message to your
email to let you know you have been tagged in a post or something similar.
• Push Notifications: Notifications that appear when you're not actively using Facebook.

Created by Michelle for OLLI@WVU 11
How to Delete Facebook
First, remember that Facebook and Messenger are linked, so deleting your Facebook account also
deletes your access to Messenger. If you currently use Messenger you will want to make sure you have
a new messaging app in place before ditching Facebook. You will also want to inform your family and
friends you are deleting messenger, so you can come up with an alternate way of keeping in touch.
Secondly, you may want to download and save all your Facebook data. You will need to do this
through a web browser, not the phone or tablet app.
Thirdly, you will want to make sure you do not have any accounts, apps, or websites that use your
Facebook login. If you do, you will need to change the login information for every site or app you want
to keep after deleting your Facebook account.
Once you’ve got your backups and alternatives in place, delete (or inactivate) Facebook and
Messenger from your phone and/or tablet. This does NOT delete your account, it just makes it harder
for Facebook to track you and collect data about you.
Some people believe in going through and deleting all your past Facebook posts and pictures,
however, if you have been on Facebook for a while, this process could take days, meanwhile all your
data is still backed up somewhere on one of Facebook’s servers.
Finally, you can deactivate or delete your account. Deactivating means the account is taken down
temporarily—and you can also use Messenger even with a deactivated Facebook account.
Once you’ve done all that, it’s time to do the same thing for Instagram and Whatsapp.
Because Facebook is constantly changing its format and settings around, here are several different
links with step-by-step instructions for deactivating or deleting your Facebook Account.
How to deactivate or delete your Facebook account
https://www.malwarebytes.com/blog/news/2021/06/how-to-deactivate-or-delete-your-facebook-
account
How to Delete Your Facebook Account https://www.pcmag.com/how-to/how-to-delete-your-
facebook-account
Deleting Facebook? Follow These Steps Carefully https://www.cnet.com/tech/services-and-
software/deleting-facebook-follow-these-steps-carefully
How to delete Facebook, Instagram and WhatsApp—and take your data with you
https://www.popsci.com/diy/how-to-delete-facebook
How to Permanently Delete Your Facebook Account https://www.wired.com/story/how-to-delete-
your-facebook-account
Created by Michelle for OLLI@WVU 12
Facebook Website
You can access the Facebook website on any device—including a phone or tablet. Facebook has
worked to make the app a more user-friendly and has deliberately broken Messenger if you attempt to
access it via the website on a phone. But otherwise you can do anything on the website you can on the
phone or tablet app.
News Feed (Browser)
Hiding Posts (Browser)
1. Click on the ellipse (…) beside the post that offends you.
2. From the menu, select your desired option.
Hide post
Hide this specific post from your wall / news feed. This is
good if you want to ignore a single, specific post.
Snooze for 30 days
Hide posts from this person for a month. This is something
that is useful in the month before an election.
Hide all from / Unfollow
This allows you to stop seeing posts from someone, but still
remain friends with them; you can see their posts by going to
their wall.
News Feed Preferences (Browser)
1. In the top right corner of the Facebook window, click on your
Account icon (the circle with your profile picture).
2. From the drop-down menu select Settings & privacy.
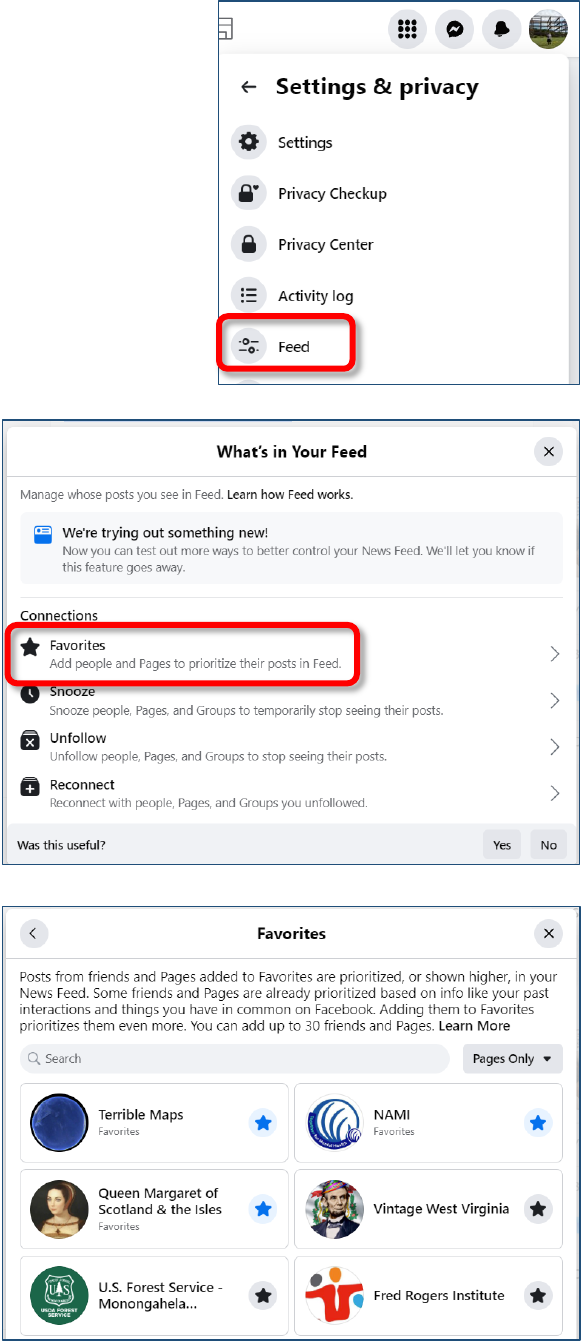
Created by Michelle for OLLI@WVU 13
3. In the Settings & Privacy section, select Feed.
4. In the What’s in Your Feed dialog box,
select Favorites.
5. Click the star icon beside the picture of
someone whose posts you want to make
sure you see.
6. Once you’re finished, click the bracket
icon in the top left corner to return to
your settings or the X icon in the top right
corner to close all the settings.
Created by Michelle for OLLI@WVU 14
Writing Posts (Browser)
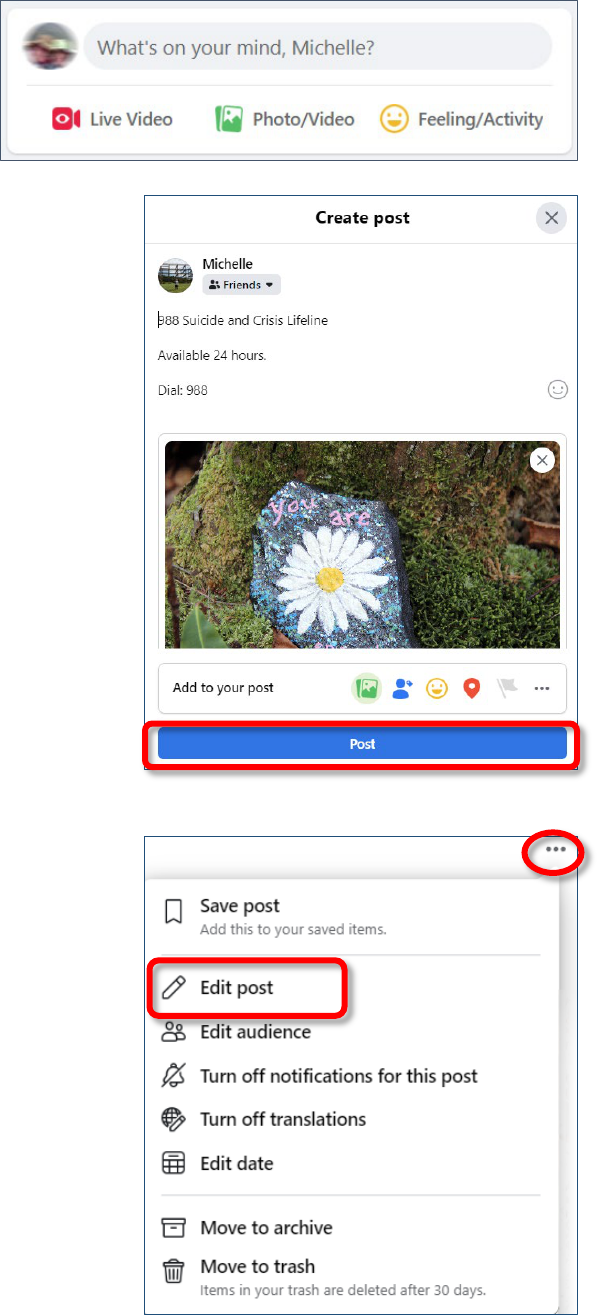
1. In your newsfeed or on your profile, click
in the post area.
2. Where it says What’s on your mind, enter what you
want to say. Click the links to add pictures, tag friends,
or add emoticons. You can also drag pictures from
windows explorer into the post to add them.
3. Once you’ve added everything, click Post.
Editing Posts (Browser)
1. Once you have created a post, you can edit or delete it.
In the top right corner of your live post, click the
ellipse (…).
2. From the pop-up menu, select the desired option.
3. These options are also available on comments you
make to other’s posts.
Created by Michelle for OLLI@WVU 15
Settings (Browser)
Settings are where you will go to check on your privacy and security, as well as to do things like tweak
your notifications.
Accessing Your Facebook Settings (Browser)
1. In the top right corner of the Facebook window, click
on your Account icon (the circle with your profile
picture).
2. Select Settings & privacy.
3. From the menu, select Settings.
Created by Michelle for OLLI@WVU 16
Privacy (Browser)
1. Open your Facebook Settings (p 15).
2. In the left pane, select Privacy Center.
Privacy Center (Browser)
Facebook has created “Privacy Center” which has guides for learning more about the various options
in the right pane. Unfortunately this can create extra clicking around to find specific settings.
Created by Michelle for OLLI@WVU 17
To quickly find specific options, in the left pane click Settings
and then Facebook Settings.
Created by Michelle for OLLI@WVU 18
Laptop or Desktop Modifying (Many) Privacy Settings (Browser)
1. Find a setting you want to modify.
2. Click Edit.
3. At the bottom of explainer, select an option.
4. Once you have selected the desired option DO NOT CLICK Close. Clicking close will NOT save
your desired option. Instead click on a different setting (any other Edit button, for instance)
Friend Requests
Account > Settings & Privacy > Settings > Privacy > Privacy Settings and Tools > How people find
and contact you > Who can send you friend requests?
Your List Facebook Friends
Account > Settings & Privacy > Settings > Privacy > Privacy Settings and Tools > Who can see your
friends list?
Profile Visibility to Search Engines
Account > Settings & Privacy > Settings > Privacy > Privacy Settings and Tools > Do you want
search engines outside of Facebook to link to your profile?
Who Can Post on your Timeline
Account > Settings & Privacy > Settings > Privacy > Profile and Tagging > Profile
Tagged Post Visibility
Account > Settings & Privacy > Settings > Privacy > Profile and Tagging > Tagging
Review of Tagged Posts
Account > Settings & Privacy > Settings > Privacy > Profile and Tagging > Reviewing
Location History
Location history is for the Facebook app on your mobile device. Through the website you can toggle it
on or off
Created by Michelle for OLLI@WVU 19
Notifications (Browser)
Account > Settings & Privacy > Settings > Notifications
• Comments
• Tags
• Friend Requests
• Browser Notifications
• Email Notifications
Logged Actions
Account > Settings & Privacy > Activity Log
Ad Preferences
Account > Settings & Privacy > Settings > Ads > Ad Settings
• Partner Data
• Demographic Categories
• Ads shown off of
Facebook
• Social Interactions
Video Auto-Play
Account > Settings & Privacy > Settings > Videos
Changing Your Password
Account > Settings & Privacy > Settings > Security and login > Login
Two-Factor Authentication
Account > Settings & Privacy > Settings > Security and login > Two-Factor Authentication
Close Your Account
Account > Settings & Privacy > Settings > Privacy > Your Facebook information > Deactivation
and deletion
Created by Michelle for OLLI@WVU 20
Apps within Facebook (Browser)
As we saw with the Cambridge Analytica scandal, Facebook apps have disseminated your data in ways
you probably are not comfortable with. It’s important to see what apps have access to your
information, and to remove apps that are not integral to your Facebook experience.
Seeing Your Facebook Apps & Games (Browser)
1. Open your Settings.
2. Select Settings & privacy, then click Settings.
3. Select Apps and Websites in the left side menu.
Removing Apps & Games (Browser)
1. In the list of active apps, find the app you want to remove.
2. To the right of the app is a very faint check box. Click inside that box to select the app (or apps) to
be deleted.
3. Click the Remove button.
4. A dialog box opens making sure you want to remove the app. Place a check in the box beside the
text asking if you want to delete all posts, photos and videos.
5. Click Remove.
Blocking Apps & Games (Browser)
1. Click your profile picture in the top right of Facebook.
2. Select Settings & privacy, then click Settings.
3. Click Security and login in the left menu.
4. Click Apps and Websites in the left menu.
5. Scroll down to Preferences, then next to Apps, websites and games, click Turn Off.
Messenger (Browser)
Using Facebook Messenger generally gives people the ability to see if you are online. I do not
recommend using the Facebook Messenger App on your mobile device, for privacy and security
reasons, so we’re going to look at FB messenger in the web browser.
Facebook Chat Options (Browser)
One of the ways Facebook pushes you to use Facebook Chat / Messenger is by putting it right in your
face. Luckily, you can close your chat box and turn off your active status. This will keep people from
knowing when you are online.
Using Facebook Messenger in Your Browser
If you are not using the Messenger app or the chat box, Facebook is going to make it more annoying
for you by forcing you to go to a separate page. Just keep in mind that Facebook is making things less
easy precisely so you will use the app. Although it is not as convenient, I recommend having private
conversations through a messaging app, such as Skype or Signal.
Created by Michelle for OLLI@WVU 21
Using Messenger in Your Browser
1. In the top left corner of the Facebook window, beneath
your news feed, click on the Messenger link.
2. A list of ongoing chats appears in the left pane. Click on
any chat to add to the message thread.
OR
Click the New Message icon to create being a new
chat.
Turning off Active Status
1. Open Messenger.
2. Click the Options (ellipse) icon
3. From the drop-down menu, select Preferences.
Created by Michelle for OLLI@WVU 22
4. Toggle Show when you’re active.
5. Click the X in the top right corner.
Finding Missed Chat Messages
1. If you are not already a friend with someone, Facebook
hides those conversations in a folder called Message
Requests.
2. Check this folder occasionally to see if anyone has tried
to contact you.
Created by Michelle for OLLI@WVU 23
Facebook App on Android
Messenger
Settings
Notifications
News Feed
Write New
Post
Created by Michelle for OLLI@WVU 24
News Feed (Android)
Hiding Posts (Android)
1. Click on the ellipse (…) beside the post that offends
you.
2. From the menu, select your desired option.
Hide post
Hide this specific post from your wall / news feed. This is
good if you want to ignore a single, specific post.
Snooze for 30 days
Hide posts from this person for a month. This is
something that is useful in the month before an election.
Hide all from / Unfollow
This allows you to stop seeing posts from someone, but
still remain friends with them; you can see their posts by going to their wall.
Facebook Settings (Android)
Facebook is constantly modifying and changing their website and app, so the easiest way to find
anything is to go to settings and then search for the specific setting you want to change.
Settings (Android)
1. In the upper right corner of the Facebook window, click the
Settings icon.
2. In the menu that appears, click the Gear (settings) icon.
Created by Michelle for OLLI@WVU 25
3. Tap in the Search Settings box.
4. Start to tap in the name of the settings you want to modify,
but as “notifications” or “privacy”.
5. As soon as you see your desired option appear, tap it.
Some of the important settings you will want to check are listed on page 8.
Created by Michelle for OLLI@WVU 26
Posts (Android)
Writing Posts (Android)
1. In your newsfeed or on your profile, tap in the post area.
2. Type whatever you want to say. Tap the links to add pictures,
tag friends, or add emoticons.
3. Once you’ve added everything, tap Post in the top right
corner.
4. Once you have created a post, you have the option to edit or
delete what you posted. In the top right corner of your live
post, click the ellipse (…).
5. From the menu that appears, select the desired option.
6. The ellipse is also available to edit or delete comments you
make to others’ posts.
Created by Michelle for OLLI@WVU 27
Location Settings (Android)
1. Open your Settings.
2. Search for Location.
3. Facebook will act like it is vitally important it knows
where you are at all times. It is NOT.
4. Toggle OFF the setting to give Facebook Background
Location. Facebook definitely does NOT need to know
where you are when you are not using the app.
5. Select Location Services (under Device Setting) and
change this setting to Never. Or if you use Check-in,
you can set it to when you are actively using the app.
But I highly recommend Never.
6. You should also clear your location history and tell
Facebook is cannot build a location history. This won’t
change what information Facebook has used in the
past, but it will keep Facebook from using your location
going forward.
Created by Michelle for OLLI@WVU 28
Facebook App on iOS
Menu
Notifications
Home
Settings
Write
Post
Created by Michelle for OLLI@WVU 29
News Feed (iOS)
Hiding Posts (iOS)
1. Click on the ellipse (…) beside the post that offends you.
2. From the menu, select your desired option.
Posts (iOS)
Writing Posts (iOS)
1. In your newsfeed or on your profile, tap in the
post area.
2. Tap in the What’s on your mind area and
type what you want to say. Click the links along
the bottom to add pictures, tag friends, or add
emoticons.
3. Once you’ve added everything, tap Post.
4. Once you have created a post, you have the
option to edit or delete what you posted. In the
top right corner of your live post, click the
ellipse (…).
5. From the menu that appears, select the desired
option.
6. The ellipse is also available on comments you
make to others posts to edit or delete.
Created by Michelle for OLLI@WVU 30
Facebook Settings (iOS)
Obviously, my first recommendation is to NOT use the Facebook app on your phone, but if you are
going to use the app, there are definitely settings you should delve into.
Accessing Facebook Settings (iOS)
1. Open the Facebook app.
2. In the lower right corner, click the three parallel lines over the word More and then select
Settings & privacy.
3. Scroll down through the list until you see Settings & Privacy.
4. The menu expands out, select Settings.
OR
1. In the top right corner click the down arrow beside your name, and from the menu select
Settings.
Some of the important settings you will want to check are listed on page 8.
Location Settings (iOS)
In general, unless you use Check-in, there is no reason to allow Facebook to know your location. I
recommend turning all location settings off. If this setting has been on, assume that Facebook knows
precisely where you live, and all the places you frequently visit, including the homes and family
members and your favorite stores.
Accessing Your Location Settings (iOS)
1. Open your Settings, then scroll down to the Security section.
2. Select Location.
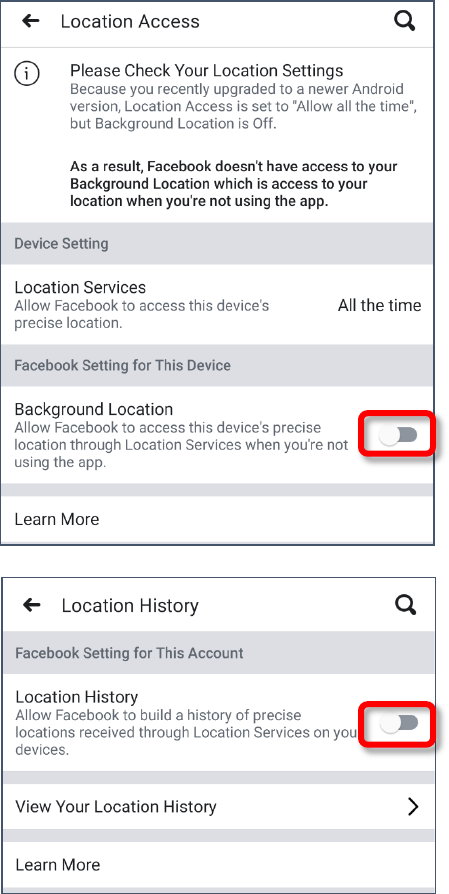
Created by Michelle for OLLI@WVU 31
3. Facebook will act like it is vitally important it knows
where you are at all times. It is NOT.
4. Toggle OFF the setting to give Facebook Background
Location. Facebook definitely does NOT need to know
where you are when you are not using the app.
5. Select Location Services (under Device Setting) and
change this setting to Never. Or if you use Check-in,
you can set it to when you are actively using the app.
But I highly recommend Never.
6. You should also clear your location history and tell
Facebook is cannot build a location history. This won’t
change what information Facebook has used in the
past, but it will keep Facebook from using your location
going forward.

Created by Michelle for OLLI@WVU 32
Web Browsers
Product
Site
Chrome
https://www.google.com/chrome/
Firefox
https://www.mozilla.org/en-US/firefox/new/
Opera
https://www.opera.com/
Web Browser Add-Ons
Product
Availability
Site
AdBlock Plus
Firefox, Chrome, Safari
https://adblockplus.org/
Disconnect
Firefox, Chrome, Safari, IE
https://disconnect.me/disconnect
Do Not Track Me
Firefox, Chrome, Opera, Safari, IE
https://abine.com/index.html
Ghostery
Firefox, Chrome, Safari, IE
https://www.ghostery.com/
HTTPS Everywhere
Firefox, Chrome, Opera
https://www.ghostery.com/
Texting Apps that Work over WiFi
Whatsapp: https://www.whatsapp.com/
Telegram: https://telegram.org/
Snapchat: https://www.snapchat.com/
Skype: https://www.skype.com/en/
Signal: https://signal.org/
Hangouts: https://hangouts.google.com/
Phone Apps
Closing Apps on an Android Device
1. Tap the Recent Applications Menu button, usually at the lower left of the screen. A list of open
apps appears
2. To close an individual app, click the x beside the app or swipe right on the app.
3. To close all open apps, if available, tap Close All.
To be clear, stopping an app frequently leaves parts of that app still running in the background. To
end all processes of that app, you need to force stop the app.
To Force Stop Apps on an Android Device
1. Open your device settings. (Typically available from the list off all applications or by pulling down
from the top of the screen to open the system tray, and tapping the gear icon.)
2. From the list of available settings, choose Apps or Applications. (Depending upon your phone.)
3. Scroll through the list to find the specific app you want to close and/or keep from running in the
background.
4. Towards the top of the screen, tap the Force Stop button.
5. The device asks if you are sure you want to do this, tap Force Stop.
Closing Apps on an iOS Device
1. Double tap on the home button to bring up a screen that displays the open apps.
OR
Swipe up twice from the bottom of the screen.
2. Drag an app up towards the top of the screen to close it.
Created by Michelle for OLLI@WVU 33
Emoticons
(.V.)
Alien
O:-)
Angel
X-(
Angry
~:0
Baby
:-D
Big Grin
(*v*)
Bird
:-#
Braces
</3
Broken
Heart
=^.^=
Cat
*<:o)
Clown
O.o
Confused
B-)
Cool
:_(
Crying
:'(
Crying
\:D/
Dancing
*-*
Dazed
:o3
Dog
#-o
Doh!
:*)
Drunk
//_^
Emo
>:)
Evil Grin
<><
Fish
:-(
Frown
:(
Frown
:-(
Frowning
=P
Frustrated
:-P
Frustrated
8-)
Glasses
$_$
Greedy
:->
Grin
=)
Happy
:-)
Happy
:)
Happy
#
Hashtag
<3
Heart
{}
Hug
:-|
Indifferent
X-p
Joking
:-)*
Kiss
:-*
Kiss
:*
Kiss
(-}{-)
Kissing
XD
Laughing
=D
Laughing
Out Loud
)-:
Left-
handed
Sad Face
(-:
Left-
handed
Smiley
Face
<3
Love
=/
Mad
:-)(-:
Married
@
Mention
<:3)~
Mouse
~,~
Napping
:-B
Nerd
^_^
Overjoyed
<l:0
Partying
:-/
Perplexed
=8)
Pig
@~)~~~~
Rose
=(
Sad
:-(
Sad
:(
Sad
:S
Sarcastic
:-@
Screaming
=O
Shocked
:-o
Shocked
:-)
Smile
:)
Smile
:-Q
Smoking
:>
Smug
:P
Sticking
Tongue
Out
:o
Surprised
:-J
Tongue in
Cheek
:-&
Tongue
Tied
=-O
Uh-oh
:-\
Undecided
:-E
Vampire
=D
Very
Happy
;-)
Winking
;)
Winking
|-O
Yawn
8-#
Zombie
34
Acronyms
AF: As (naughty word)
AFK: Away from Keyboard
BTW: By the Way
B/C: Because
BFF: Best Friends Forever
BRB: Be Right Back
CU: See You
CYT: See You Tomorrow
DGMW: Don’t Get Me Wrong
EOD: End of Discussion
EOM: End of Message
F2F: Face to Face
FAQ: Frequently Asked Questions
(pronounced fak to rhyme with pack)
FREX: For Example
FTW: For the Win
FWIW: For What It’s Worth
FYI: For Your Information
GR8: Great
HTH: Hope This Helps
ICYMI: In Case You Missed It
IDC: I Don’t Care
IDK: I Don’t Know
IIRC: If I Remember/Recall Correctly
IMHO: In My Humble Opinion
IMO: In My Opinion
IOW: In Other Words
IRL: In Real Life
J/K: Just Kidding
L8R: Later
LOL: Laugh(ing) Out Loud
MYOB: Mind Your Own Business
noob / n00b: Newbie
NNTR: No Need to Reply
NOYB: None of Your Business
NP: No Problem
NRN: No Reply Needed
NSFW: Not Safe for Work
OMG: Oh My God
OMY: On My Way
OTOH: On the Other Hand
OT: Off Topic
OTP: On the Phone
ROTFL: Rolling on the Floor Laughing
RTFM: Read the Fantastic Manual
RU: Are You
SFLR: Sorry for Late Reply
SO: Significant Other
TBC: To Be Continued
THX: Thanks
TIA: Thanks in Advance
TL;DR: Too Long Didn’t Read
TMI: Too Much Information
TTYL: Talk to You Later
TUVM: Thank You Very Much
TYT: Take Your Time
UR: You Are / Your
w00t / W00T: Hooray! Yay! Yippee!
W8: Wait
WFM: Works for Me
WRT: With Regard To
WTH: What the H(eck)
WTF: What the (naughty word)
YMMV: Your Mileage May Vary

35
Technology Glossary
Add-on
An accessory piece of software designed to increase the capability of the software to which it is
appended.
Address Bar
In a web browser or windows explorer, it is a rectangle, usually towards the top of the window, that
shows you the current location or address of your web page or file.
Address Book
See Contacts
Alexa
Amazon’s virtual assistant.
Algorithm
A set-of rules to be followed in calculations or problem-solving operations. Algorithms are frequently
used to manipulate data sets.
Android
Googles mobile operating system, built on open source software.
Anti-Virus
A program that protects you from malicious software. Most anti-virus programs have options for
purchasing additional security measures such as firewalls, email scanning, etc.
App
Short for Application.
Apple ID
This is the username and password that you create with Apple to link a specific device to your Apple
account. If you have an iPad and an iPhone, you use the same Apple ID with both of those devices.
Apple
Technology company that designs and develops hardware and software.
Application
An application is a piece of software that lets your device do something, like play music or give
directions. An application is the same thing is a program.
Autocorrect
Auto correct is when your phone automatically changes what you were typing to what it thought you
wanted to type.
Autoplay
When you visit a website and music or video starts playing without asking.
AVI
Audio Video Interleave. A multimedia format for audio and video files.
Backup
A copy of computer data that is taken and stored somewhere else, to be used in the event of data loss.
BCC
Blind carbon copy. Covertly send a copy of the message to a third party. The primary recipient cannot
see the person was added.
Biometric
Unique physical characteristics that are be used for recognition. The most common types of biometric
identifiers are fingerprints, voice, face, iris, and palm/finger veins.

36
Blockchain
Also Block Chain. A list of records (blocks) linked using cryptography. These records are a
cryptographic hash of the previous block, a timestamp, and transaction data. Blockchains are
generally used on a peer-to-peer network. Data in one block cannot be altered without changing all
other blocks.
Bluetooth
A wireless technology that allows data to be shared over short distances using short-wave UHF radio
signal. The name comes from Harald "Bluetooth" Gormsson, king of Denmark and Norway, who
united the Scandinavians.
Boolean
A system of logical propositions. Common Boolean operators: AND, OR, NOT, “ “, ( ) . Based on the
work of George Boole.
Browser Add-on
See Browser Extension.
Browser Extension
A small software module that is used to customize a web browser.
Browser Hijack
Where a malicious piece of software modifies a web browser’s settings without your permission.
Browser
Short for Web Browser.
Brute Force Attack
Where a hacker tries many passwords for passphrases in an attempt to break into an account. The
longer the password (or passphrase) the harder it is for someone to succeed with this type of attack.
Byte
A unit of digital information that consists of eight bits. A byte is the number of bits used to encode a
single character of text.
Cache
Temporary storage space that allows your computer to quickly bring up information, such as
previously viewed web pages.
Cambridge Analytica
A British political consulting firm that used misappropriated digital assets, data mining, and other
processes to influence political elections around the world.
CC
Carbon copy. Send a copy of the message to someone else. The primary recipient can see this person
received the message.
Cellular Data
The connection a cell phone makes to a cell tower that allows you to do things like surf the internet,
download emails, and send MMS messages.
Cloud
Storage that is physically somewhere other than where you are. Cloud storage is generally accessible
from multiple devices, because those files are stored on a hard drive that belongs to a company that
hosts the cloud service. Cloud storage is like a self-storage unit for your electronic files, except you can
access your stuff from anywhere.
37
Cloud Service
A service provided by a third party or company that allows you to provide access to files and
applications remotely.
Codec
A device or program that encodes/decodes a data stream, such as an audio file, for storage.
Contacts / Contact List
A collection of screen names and the various data associated with them, such as email addresses and
telephone numbers.
Cookie
A piece of data that a website saves on your computer. Cookies were designed to save user
information such as preferences or logins but can sometimes be read by third parties. Cookies are also
used to collect browsing data long-term.
Cortana
Microsoft’s virtual assistant.
CPU
Central Processing Unit. The bit of a computer or electronic device that processes information.
Cryptocurrency
A digital asset that uses strong cryptography and is designed to work as a form of money. They used
decentralized control, or a public financial database to keep track of who owns what.
Cryptography
Greek for “hidden writing”, it is the study of secure communication—creating protocols to keep third
parties from reading private messages.
Data Breach
The release of secure or private information. A data breach can be accidental or malicious, such as
when an individual hacks into a system to steal information.
Database
An organized collection of information. Complicated databases link information between multiple
tables allowing for analysis of the contained information. An address book is a basic database.
Denial of Service Attack (DOS)
A cyber-attack where the malefactor seeks to make a network resource (such as a website) unavailable
by flooding the target with requests or visits.
Directory
A system that catalogs / organizes computer files.
Displayport
A high-quality audio-visual cable capable of transmitting HD and 4k.
DNS
Domain Name System. The phonebook of the Internet.
DNS Hijacking
Where a malefactor redirects visitors from a valid website to a different destination—often one that
exists to steal data.
Domain Name
The string of text that identifies a place on the Web. A basic domain name is a word or abbreviation
followed by a period followed by the domain extension: wvu.edu

38
Domain
The sometimes arbitrary grouping that designates what a website does or where it is based. The most
common domains are .com .net .edu and .org. The domain is what you should check first when you
want to verify the authenticity of a website.
Download
To move data and files from the internet or a server to your computer or mobile device.
DRM
Digital Rights Management. A format that protects electronic media from being illegally copied.
DVD
Digital Video Disc / Digital Versatile Disc. A digital optical disc data storage system.
DVI
Digital Video Interface. A video display interface that connects your computer to your monitor.
Email Header
The portion of an email message that contains the routing information. The header can be used to
help determine if a message is fraudulent.
Email
Email is an electronic letter sent from one email address to another email address. Email addresses
always have an @ (at sign) in them. Sending an email on your phone requires the use of cellular data.
Each email address is unique, and email addresses are often used as unique identifiers or login
credentials by databases.
Emoji
Small images used to represent emotions, ideas, or expressions.
Emoticons
Representations of facial expressions using keyboard characters. These are used to portray moods or
feelings. For example, a smiling face could be :) or
Encryption
The encoding of data so that only authorized persons or devices can read/view the information. The
stronger the encryption, the more unlikely it is that a malfeasant could decode the intercepted data
through a brute force attack.
EPUB
Electronic Publication. A digital book format that allows you to read your eBook on any electronic
device. EPUB files are reflowable.
eReader
eBook reader that use black and white eInk screens that give a similar reading experience to physical
books.
Ethernet
Wired networking technology that allows multiple computers to talk to one another via a protocol (set
of rules). Ethernet is used when speed, stability, and security are needed.
EULA
End-User License Agreement. The legal contract between a software vendor and the user of that
software. It specifies the rights and restrictions which apply to the use of the software.
External Storage
Devices that store data outside of a computer or other electronic device. They are often removable,
such as USB thumb drives.

39
Facebook
An online media and networking company.
Facial Recognition
Technology capable of identifying or verifying a person from a digital image. Facial recognition can be
used to unlock an electronic device.
File Extension
Also called a filename extension or file type, is the identifier suffix for a computer file name, and tells
you the kind of program needed to open the file. By default, these extensions are hidden, but can still
be used in search. If you change a file extension, that file will most often break.
Firewall
A security system that monitors incoming and outgoing network traffic to prevent unauthorized
access to a system.
Folder
See Directory.
Follow
Choose to see another user’s posts in their content feed.
Force Stop
A way to completely stop an app that is running in the background. An app that has been closed may
still have bits active and collecting data.
GB
Gigabyte. A computer memory unit equal to 1000 megabytes. The prefix giga means 10
9
.
GIF
Graphics Interchange Format. An image format that is often used in logos and animated pictures.
Google
A technology company that specializes in services and products related to the internet.
GPS
Global Positioning System is a piece of hardware that allows a device to contact a satellite to
determine the location of the device in latitude and longitude. On most devices, software makes these
data points usable to the end user by placing them on a map.
GUI
Graphical User Interface (pronounced gooey). The windows, icons, menus, and pictures that allow
you to interact with your computer using your mouse. Windows 10 and Mac OS (Big Sur) are
operating system GUIs.
Hard Drive
A data storage devices that stores and retrieves digital data. In your computer, this is where all your
programs are installed and files saved.
Hardware
The electronic components of a device; the bits you can touch. A cell phone, a keyboard, and a CPU
are all hardware.
HD
High Definition. Generally a higher resolution and quality than standard definition video.
HDMI
High-Definition Multimedia Interface. Audio/video interface for transmitting uncompressed data.
Cable that connects your computer to your monitor, or your DVD player to your TV.
40
HDR
High Dynamic Range. A photographic process where a camera takes multiple pictures at different
exposures and combines them into a single image—this allows all areas of your image to be well-
exposed, but can also look unreal if used too much.
Heat Map
A heat map is a visual representation of data that allows you to see phenomenon as clusters or over
space.
Home Screen
The main screen of a computer or mobile device. Home screens are typically personalized by the user
so that no two home screens will look alike.
Hotspot
A type of Wireless Access Point. A device that allows you access the internet from a public place.
Hotspots are generally open and unsecured and you should assume any data you submit is visible to
people with ill-intent.
Hover text
When you hold your cursor over a hyperlink, the document should display the URL for that link. This
allows you to verify links.
http
Hypertext Transfer Protocol is how data is moved between a website and an end user.
https
Hypertext Transfer Protocol (Secure) is an encrypted form of http. This protects against interference
or snooping by third parties.
iCloud
Apple’s cloud service.
Icon
A graphic representation of a program, file or function.
Information Security
The protection of data and the mitigation of risks, generally on computer networks.
Install
A process that writes the code used to run the program (application) onto the hard drive of your
device. Installing a piece of software embeds it into the device and allows it to work.
Internet
A system of inter-connected computer networks.
iOS
Apple’s mobile operating system.
iPad
Apple’s tablet computer, running iOS.
iPhone
Apple’s cellular phone, running iOS.
iPod
Apple’s music player. The iPod is general similar to an iPhone, only without cellular service.
ISBN
International Standard Book Number. A numeric commercial book identifier that is unique for every
edition and variation of a book.

41
ISP
Internet Service Provider. Company you pay so you can have internet at home.
iTunes
Apple’s music service.
JPG / JPEG
Joint Photographic Experts Group. A lossy compression format for digital images.
Keylogger
Keystroke logger (also keyboard capture). A piece of hardware or a software program that can record
every key struck on the keyboard.
LAN
Local Area Network. A group of computers / devices that share a common communications line.
Location Bar
See address bar.
Location Services
Information from GPS, wireless access points, cell towers, and Bluetooth devices that helps your
phone know where you are.
Lock Screen
The opening screen or interface of an operating system. A lock screen keeps unauthorized users from
accessing the data and information on a device.
Lossless Compression
A form of data encoding that maintains the original quality of the file but at the cost of having a large
file size.
Lossy Compression
A form of data encoding used to reduce file size at the cost of data quality.
Mbps
Megabits Per Second. The speed of your internet service.
Messenger
An app that allows users to send text messages and images to other users in a system.
Metadata
A data set that give you information about other data. A card catalog contains metadata.
Micro-SD
Micro-Secure Digital Card. Smaller size SD card, used in phones and lightweight devices. Comes with
an adapter that allows for the transfer for files from a portable device to a computer.
MMS
Multimedia Messaging Service is a kind of text messaging that allows you to send text messages that
contain pictures or audio, as well as messages longer than 160 characters or to multiple people.
MOBI
Mobipocket. The proprietary ebook format for the Amazon Kindle. MOBI files are reflowable.
Mobile Carrier
A wireless service provider that allows users to connect portable devices (such as phones) to the
internet through a cellular service.
Mobile Data
Wireless internet access through a cellular data connection.

42
MP3
Moving Pictures Experts Group Layer-3. A coding format for digital audio.
MP4 / MPEG4
Moving Pictures Experts Group Layer-4. A coding format for digital multi-media, commonly video.
MPEG
Motion Picture Experts Group. A standard for encoding and compressing video.
NDA
Non-Disclosure Agreement. A legally binding contract where parties agree not to share sensitive or
confidential information.
Network
A group of computers connected for the purpose of sharing resources. A network can be as small as
two computers or as vast as the Internet.
News Feed
The main page of Facebook, where you see content posted by users you have chosen to follow. These
content can be text or images.
Notification
A message displayed by an electronic device to provide an alert, reminder, or other communication.
Online Chat
Real time communication over the internet through (generally short) text messages.
OS
Operating System. The base upon which software and apps are added. An Apple device generally uses
iOS (iPhones) or macOS (laptop computers). PCs typically used the Windows OS, but there are other
operating systems, such as Linux that can be installed. Non-Apple cell phones frequently use some
form of the Android OS. How your device looks and works is dependent upon the operating system
installed.
P2P
Peer-to-Peer
Passcode
This is the secret code to get into a specific device. If you have an iPhone and an iPad, they can have
different passcodes. You can sometimes use a fingerprint instead of a passcode to get into a device.
Password Manager
A program that stores electronic passwords.
Password
The secret code to access a restricted resources. Passwords are usually required to use a minimum of
eight characters, and contain special characters, such as numbers or upper case letters.
PayPal
A method of online money transfer and payments.
PDF
Portable Document Format. Once an Adobe proprietary format, now one of the most common
formats for sharing digital documents.
Peer-to-Peer
A distributed that shares tasks or work between devices of the same level.
Phishing
A fraudulent attempt to gain personal or sensitive information, by sending an email or creating a
website that pretends to be from a real company or person, but is not.

43
Play Store
Goggle’s app store, where users can download or purchase programs to run on their Android devices.
PNG
Portable Network Graphics. A lossless compression type for digital images.
Podcast
A digital audio file made available on the Internet for downloading to a computer or mobile device,
typically available as a series, new installments of which can be received by subscribers automatically.
Post
A message, comment, image, or other item that is placed on the internet, generally on a website.
Predictive Text
An input technology that guesses what you want to type both from what you are currently typing and,
if you have allowed the software to learn, from what you have typed in the past. Predictive text makes
typing faster and easier if you have good software on the back end.
Privacy
The information that is shared between your device and the external resources to which it is
connected, as well as how that information is used, and with whom that information is shared.
Program
A program is a piece of software that lets your device do something like send a text message or video
chat. A program is the same thing as an application.
Public Network
An electronic connection where the traffic between devices is visible to anyone.
Reflowable
An ebook format that layout depending upon the output device. MOBI and EPUB are reflowable
formats, which means the number of words on the page change, depending upon the page / text size.
Reply All
A response to an electronic message that is returned to ALL recipients of the original message.
Reply
A response to an electronic message.
Ripping
Extracting digital content from a container, such as a CD or DVD. Ripping a CD means that the music
is copied without loss from the CD to your computer.
ROT-13
One of the most basic forms of encryption; a substitution encryption where characters are rotated 13
places.
Router
A networking device that forwards data between networks.
RTFM
Read The Fantastic Manual.
Scraping
Web scraping, web harvesting, web data extraction is extracting data from websites—gathering up
information available on a public website.
SD
Standard Definition. The lowest quality rating for digital streaming.
44
SD Card
Secure Digital Card. Removable memory that is used in devices like cameras, because it can be easily
switched out when full. Allows for easy transfer of files from device to computer without a cable.
Search
A computer command that allows you to find specific files on your computer that meet a designated
category, such as file type, or date modified.
Search Engine
A software system designed to find information on the web. The results from a search engine can be
webpages, files, or images. Generally, behind the scenes a program runs an algorithm that crawls
through the web cataloging everything it sees. This catalog is then organized by a different program
where pages are associated with various terms.
Security
Protecting electronic systems from theft or damage. This can be protection from physical theft, but
often refers to electronic damage, where systems can be disrupted or data stolen.
Server
A device (or program) that allows you to access something not on the device you are physically
touching. A mail server stores your email and drops it to your device upon request. A web server
allows you to connect to the internet.
Settings
An app that allows you to customize your computer, device, or program.
Siri
Apple’s personal assistant.
Smart Device
An electronic device that connects to other devices or the internet through a wireless protocol such as
Bluetooth or Wi-Fi.
Smart TV
A television with a network port to allow you to watch streaming services (and other internet content)
without having to use an additional device.
SMS
Short Messaging Service. A brief message that is sent from one phone number to another phone
number. SMS does not use cellular data.
Snooping
Unauthorized listening in to data transmission.
Snopes
One of the first internet fact-checking resources, Snopes started as a site to debunk urban legends, but
expanded into general fact-checking. (https://www.snopes.com/)
Social Media
Interactive computer technologies and websites that allow for the sharing of information. Facebook is
the most famous social media site, and allows friends to connect automatically, but LinkedIn is
another type of social networking site, that focuses on career and job networking.
Software
The programs that run on your computer or phone. Can also be called an application.
Sort
To organize information in a prescribed sequence, such as alphabetically, or oldest to newest.

45
Spam
Unsolicited electronic messages (especially advertising).
Spoofing
When a person or program pretends to be someone else, by falsifying data, to gain access to your
account or data.
Spyware
A piece of malicious software that secretly installs itself to gather information about the user or
device.
SSD
Solid State Drive. A storage device for your computer that saves data on chips instead of a mechanical
platters.
Status Bar
A graphical element, usually at the top or bottom of a device’s screen, that displays information about
the state of the device. Some settings commonly found on the status bar are sound/volume, time, and
battery life.
Streaming Device
An object, such as Roku stick or Fire stick, you purchase that plugs into your existing TV so you watch
video through the device on your existing television.
Streaming Service
An online provider of entertainment (music, movies, etc.) that delivers the content via an Internet
connection to the subscriber's computer
Sync
See synchronize.
Synchronize
When a file is synced, changes to that file are saved are pushed from one device to all other devices
with access to that file, via a remote server.
Tag / Tagging
A keyword or term added to the metadata of a piece of information. In social media, when someone is
tagged, they are alerted to a post made by another user.
Taskbar
A graphical user interface (GUI) that is typically along the bottom of your window, and usually shows
you what programs are actively running as well as important information about the operating system.
TB
Terabyte. A measure of computer storage equal to 1000 gigabytes or trillion bytes. The prefix tera
means 10
12
.
Terms of Service
The rules you agree to abide by when you sign up use an online service.
Text Message
A brief message that is sent from one phone number to another phone number via a protocol called
SMS. Text messages are generally limited to 160 characters, and messages with more characters than
that will be broken down into multiple messages when sent. Text messages are asynchronous:
a message sent to someone whose phone is off is delivered when their phone is turned back on. Text
messages generally do not require cellular data but do require a cellular connection.
Thumb Drive
USB Flash Drive

46
TIFF / TIF
Tag Image File Format. Lossless digital image format that was developed originally for scanners as an
alternative to multiple proprietary formats.
Timeline
A display of items in chronological order. Twitter has a timeline; Facebook has a news feed.
TL;DR
Too Long, Didn’t Read
TOS
Terms of Service
Trojans
A type of malicious computer virus that presents itself as a useful item, such as a document.
Two-Factor Authentication
This is a way to make both your device and your account more secure. When you log into your Apple
ID on a new iPad (or iPhone) for the first time OR you log into iCloud from a computer you have
never used before, Apple wants you to verify that YOU are the person attempting to access your
account.
TXT
Text message.
Unfollow
To stop seeing a user’s posts in your timeline or news feed. On Facebook, you can unfollow someone
by still remain friends with them.
Uninstall
The removal or a software program or application from the operating system of a device. Although
uninstall removes the visible aspects of a program, there are often bits and pieces of the program left
behind.
Unique Identifier
A piece of data that is unique to a record. Telephone numbers and email addresses are often used as
unique identifiers, because no two individuals have the same ones. Unique identifiers allow data
records to be linked across databases.
Upload
To move files from your computer to a cloud service or network.
URL
Uniform Resource Locator is the address of a space on the web. Every website has a unique address,
and that address can often tell you something about the web page you are visiting.
URL Bar
See address bar.
USB
Universal Serial Bus. This is the industry standard for cables that connect devices and their
peripherals through a wire. This connection can be used for both communication and power. There
are several types of USB connections: USB-A, USB-A 3.0, mini-USB, micro-USB, and the newest
standard, USB-C.
USB Flash Drive
Also: USB thumb drive. A small USB data storage device that is removable, rewritable, and can be
easily carried in a pocket.
47
User Data
Any type of data generated by people interacting with software programs. User data includes:
Explicit Data, which is given by a user directly such as name, address, email, and phone number;
Implicit Data, which is not provided by the user directly but gleaned through analysis of user
interactions, such as pages visited, session duration, or type of device; and finally External Data which
has been gathered from third parties with whom an organization has a relationship.
Username
Also called account name, login ID, user ID. The credentials you use to access an electronic resources,
such as your computer or a website. Every account on a website or device must be unique to that
service, so as to keep account information separate.
VGA
Video Graphics Array. A connector that takes video signal from a computer and takes it to the monitor
(or projector).
Virtual Personal Assistant
A software program that preforms tasks or services based upon verbal commands. Some of the most
well-known services are Siri and Alexa.
Viruses
A piece of malicious software that inserts itself into another software program that it uses to replicate
itself. Ransomware is a software virus.
WAV
Waveform Audio File Format. An audio file standard for uncompressed audio.
Web
Also called the World Wide Web, this is an information space on the Internet that is accessible from
devices such as computers, cell phones, and tablets, using a URL as the address.
Web Browser
A software program that allows you to access sites on the Internet, or web.
Web Cookie
See Cookie.
Website
a location connected to the Internet that maintains one or more pages on the World Wide Web
Wi-Fi
Short for wireless (the “fi” is an arbitrary syllable added on)
Widget
A graphical element that displays information or provides quick access to certain parts of an app.
Mobile devices frequently have a weather widget that is linked to your weather app, and which tells
you the current temperature and forecast.
Wireless Access Point
A device that allows your device to access the internet. If a wireless access point (or router) does not
have a password, it is unsecure, and you should assume that anyone can see what you are doing on
your device.
Wireless Router
A piece of hardware that allows devices to connect to the internet without being plugged into the wall.
Your wireless at home should be password protected, so that strangers cannot access all devices in
your home using that wireless network.

48
Wireless
A technology that allows computers to connect to a network and/or the internet without using a
physical connection. Wireless is available in an area when a wireless access point (also called a
hotspot) has been created and made accessible to devices. Public wireless is less secure and caution
should be used (ie, don’t make purchases or send private emails over a wireless network). Private
wireless networks (such as in your home) should be secured with a password.
World Wide Web
An information system on the Internet which allows documents to be connected to other documents
by hypertext links, enabling the user to search for information by moving from one document to
another.
References
An Ugly Truth: Inside Facebook's Battle for Domination (2021) Sheera Frenkel, Cecilia Kang
Mindf*ck: Cambridge Analytica and the Plot to Break America (2019) Wylie, Christopher
A recent history of Facebook scandals (2019)
https://www.trtworld.com/magazine/a-recent-history-of-facebook-scandals-26157
Adam D. I. Kramer, Jamie E. Guillory, and Jeffrey T. Hancock “Experimental evidence of massive-
scale emotional contagion through social networks” (2014) PNAS 111 (24) 8788–8790
Censorship by Elizabeth R. Purdy (The First Amendment Encyclopedia) https://www.mtsu.edu/first-
amendment/article/896/censorship
Everything you've ever posted publicly on Facebook has probably been harvested. So what?
https://www.cbc.ca/news/technology/facebook-scraping-public-profile-data-so-what-where-why-
1.4610146
Explained: All about Facebook's biggest controversy since Cambridge Analytica (2021)
https://www.moneycontrol.com/news/business/explained-all-about-facebooks-biggest-controversy-
since-cambridge-analytica-7542651.html
Facebook Approved Ads With Coronavirus Misinformation (Consumer Reports – 2020)
https://www.consumerreports.org/social-media/facebook-approved-ads-with-coronavirus-
misinformation
Facebook attacked over app that reveals period dates of its users (Guardian - 2019)
https://www.theguardian.com/technology/2019/feb/23/facebook-app-data-leaks
Facebook says Apple iOS privacy change will result in $10 billion revenue hit this year (2022)
https://www.cnbc.com/2022/02/02/facebook-says-apple-ios-privacy-change-will-cost-10-billion-
this-year.html
Facebook turned over chat messages between mother and daughter now charged over abortion
(2022) https://www.nbcnews.com/tech/tech-news/facebook-turned-chat-messages-mother-
daughter-now-charged-abortion-rcna42185

49
Facebook, Cambridge Analytica and data mining: What you need to know (CNet - 2018)
https://www.cnet.com/news/facebook-cambridge-analytica-data-mining-and-trump-what-you-need-
to-know/
Facebook, Inc., FTC v. : https://www.ftc.gov/legal-library/browse/cases-proceedings/191-0134-
facebook-inc-ftc-v
Facebook’s Notifications Are Out of Control. Here’s How to Tame Them. (NY Times 2019)
https://www.nytimes.com/2019/05/30/smarter-living/stop-facebook-notifications.html
Facebook’s Secret Censorship Rules Protect White Men From Hate Speech But Not Black Children
(ProPublica - 2017)
https://www.propublica.org/article/facebook-hate-speech-censorship-internal-documents-
algorithms
Facebook's latest controversy has echoes of Cambridge Analytica scandal (CNN - 2019)
https://www.cnn.com/2019/05/11/tech/facebook-rankwave-korean-data/index.html
Guess what? Facebook still tracks you on Android apps (even if you don't have a Facebook account)
https://privacyinternational.org/blog/2758/guess-what-facebook-still-tracks-you-android-apps-
even-if-you-dont-have-facebook-account
How the cookie became a monster (2022) https://www.npr.org/2022/11/18/1137657496/third-party-
cookie-data-tracking-internet-user-privacy
Recover Your Facebook Account if You Can’t Log In
https://www.facebook.com/help/105487009541643
How to Memoralize a Facebook Account
https://www.facebook.com/help/1506822589577997
How to Secure your Facebook Account (CNet & Lifewire)
https://www.cnet.com/how-to/secure-your-facebook-account-in-six-easy-steps/
https://www.lifewire.com/how-to-secure-your-facebook-timeline-2487774
How to Use Facebooks Privacy Settings (Consumer Reports)
https://www.consumerreports.org/privacy/facebook-privacy-settings/
If Facebook is stalking me, what about Instagram? (Washington Post, 2020)
https://www.washingtonpost.com/technology/2020/01/30/help-desk-if-facebook-is-stalking-me-
what-about-instagram
Information flow reveals prediction limits in online social activity. Nature Human Behaviour volume
3, pages 122–128 (2019) https://www.nature.com/articles/s41562-018-0510-5
Right-wing media thrives on Facebook. Whether it rules is more complicated.
https://www.vox.com/recode/21419328/facebook-conservative-bias-right-wing-crowdtangle-election
(Vox 2020)
Sensitive to claims of bias, Facebook relaxed misinformation rules for conservative pages
https://www.nbcnews.com/tech/tech-news/sensitive-claims-bias-facebook-relaxed-misinformation-
rules-conservative-pages-n1236182 (NBC 2020)

50
She risked everything to expose Facebook. Now she’s telling her story. (MIT Technology review 2021)
https://www.technologyreview.com/2021/07/29/1030260/facebook-whistleblower-sophie-zhang-
global-political-manipulation
Social Media and the Transformation of Public Space (2015)
https://journals.sagepub.com/doi/full/10.1177/2056305115622482
The Complete Guide to Facebook Privacy (Wired.com)
https://www.wired.com/story/facebook-privacy-apps-ads-friends-delete-account/
The Facebook and Cambridge Analytica scandal, explained with a simple diagram (Vox - 2018)
https://www.vox.com/policy-and-politics/2018/3/23/17151916/facebook-cambridge-analytica-
trump-diagram
The Facebook Files: A Wall Street Journal investigation : https://www.wsj.com/articles/the-
facebook-files-11631713039
The indisputable harm caused by Facebook (Washington Post 2021)
https://www.washingtonpost.com/world/2021/10/26/indisputable-harm-caused-by-facebook
The Many Identifiers in Our Pockets: A primer on mobile privacy and security (2015)
https://citizenlab.ca/2015/05/the-many-identifiers-in-our-pocket-a-primer-on-mobile-privacy-and-
security
Under Facebook’s new algorithm, conservative meme pages are outperforming all political news
pages (Media Matters - 2018)
https://www.mediamatters.org/blog/2018/07/24/under-facebook-s-new-algorithm-conservative-
meme-pages-are-outperforming-all-political-news-pages/220768
We’re Keeping Track of All of Facebook’s Scandals So You Don’t Have To (Fortune - 2018)
https://fortune.com/2018/04/06/facebook-scandals-mark-zuckerberg/
What You Don’t Know About How Facebook Uses Your Data (NYT - 2018)
https://www.nytimes.com/2018/04/11/technology/facebook-privacy-hearings.html

51
Index
User Tracking .................................................... 1
Unique Identifiers ............................................. 1
Web Cookies ..................................................... 2
Privacy .............................................................. 2
Apps Sharing Personal Data ( - 2019) .............. 2
Facebook Controversies ................................... 2
Scams ................................................................ 2
Retaining users’ deleted videos (2018) ............ 2
Data-Breaches 2018-2021 ................................ 2
Scraping Public Profiles ................................... 3
World-Wide Election Meddling ....................... 3
Rohingya (2018-2019) ...................................... 3
India (2019-2021) ............................................. 3
Russian Meddling ............................................. 3
Cambridge Analytica (2014-2018) ................... 4
Anti-Trust? ....................................................... 4
Censorship ........................................................ 5
Public Discourse and Mental Health ............... 6
Emotional Manipulation .................................. 6
And Yet… .......................................................... 6
Making Your Facebook Use More Secure ........ 7
Using Facebook ................................................ 8
Posts .................................................................. 8
Public vs Friends vs Groups ............................. 8
News Feed ......................................................... 8
Facebook Settings ............................................. 9
Activity Settings ................................................ 9
Notifications ................................................... 10
How to Delete Facebook .................................. 11
Facebook Website ............................................ 12
News Feed (Browser) ...................................... 12
News Feed Preferences (Browser) ................. 12
Writing Posts (Browser) ................................. 14
Editing Posts (Browser) .................................. 14
Settings (Browser) ........................................... 15
Accessing Your Facebook Settings (Browser) . 15
Privacy (Browser) ........................................... 16
Privacy Center (Browser) ............................... 16
Apps within Facebook (Browser) ................... 20
Messenger (Browser) ...................................... 20
Using Facebook Messenger in Your Browser 20
Facebook App on Android .............................. 23
News Feed (Android)...................................... 24
Settings (Android) .......................................... 24
Posts (Android) ............................................... 26
Facebook App on iOS ..................................... 28
News Feed (iOS) ............................................. 29
Posts (iOS) ...................................................... 29
Facebook Settings (iOS) ................................. 30
Accessing Facebook Settings (iOS) ................ 30
Location Settings (iOS) .................................. 30
Web Browsers ................................................. 32
Web Browser Add-Ons ................................... 32
Phone Apps ..................................................... 32
Closing Apps on an Android Device ............... 32
To Force Stop Apps on an Android Device .... 32
Closing Apps on an iOS Device ...................... 32
Emoticons ....................................................... 33
Acronyms ........................................................ 34
Technology Glossary ....................................... 35
References ....................................................... 48
Index ................................................................ 51
Please Support OLLI@WVU!
Osher Lifelong Learning Institute
Mountaineer Mall Unit C-17
PO Box 9123
Morgantown, WV 26506-9123
Phone Numbers:
Office: (304) 293-1793
Email Address: oll[email protected]u.edu
http://www.olliatwvu.org
